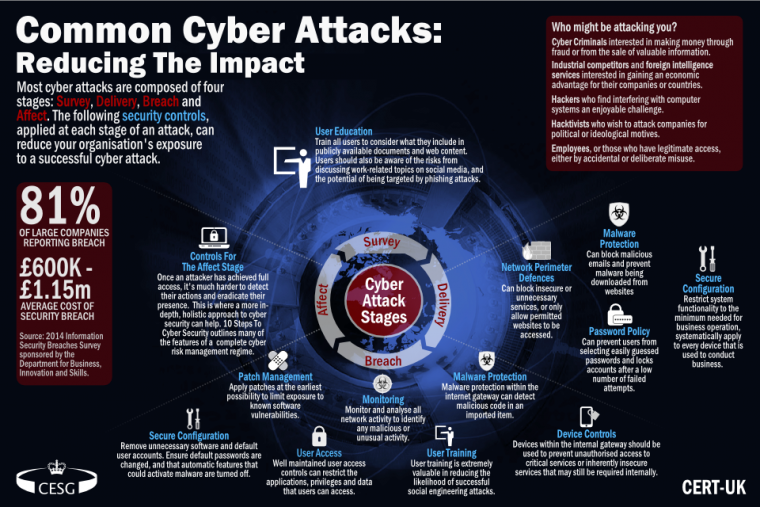
Cyberattack Details
Cdk cyberattack update – CDK, a leading provider of automotive retail software, recently fell victim to a sophisticated cyberattack that compromised sensitive data and disrupted its operations.
The recent CDK cyberattack has raised concerns about the security of sensitive data, including that held by the social security administration. While the full extent of the damage is still being assessed, it is clear that this attack highlights the need for robust cybersecurity measures to protect critical infrastructure and personal information.
The attack, which occurred on March 16, 2023, targeted CDK’s core systems, including its dealership management software (DMS) and customer relationship management (CRM) system. The attackers gained access to CDK’s network through a phishing email that tricked an employee into clicking on a malicious link.
CDK’s recent cyberattack has been making headlines, highlighting the importance of cybersecurity measures. While the aftermath of the attack continues to be assessed, sports enthusiasts are eagerly anticipating the thrilling conclusion of the Stanley Cup playoffs with Game 7. The high-stakes match promises an intense battle on the ice, with fans holding their breath as the puck drops.
As the CDK cyberattack update unfolds, we eagerly await the outcome of both this gripping sporting event and the ongoing investigation into the digital breach.
Compromised Systems and Data
- Dealership management software (DMS)
- Customer relationship management (CRM) system
- Financial data
- Customer personal information (names, addresses, phone numbers, email addresses)
Methods Used by Attackers, Cdk cyberattack update
The attackers used a combination of techniques to gain access to CDK’s systems, including:
- Phishing email
- Exploitation of a software vulnerability
- Lateral movement within CDK’s network
Impact and Response: Cdk Cyberattack Update

The cyberattack on CDK significantly disrupted the company’s operations and impacted its customers. The attack caused widespread outages of CDK’s software and services, affecting dealerships’ ability to process sales, service, and other critical functions.
In response to the attack, CDK implemented containment measures to isolate the affected systems and prevent further spread of the malware. The company also notified its customers about the attack and provided guidance on how to mitigate potential risks.
Customer Impact
- Dealerships experienced disruptions to their sales and service operations, leading to lost revenue and customer inconvenience.
- Customers faced delays in vehicle purchases, repairs, and other services due to the outages.
- CDK’s reputation among customers was potentially damaged due to the disruption of services.
Potential Consequences and Implications
- CDK’s financial performance may be negatively impacted due to lost revenue and the costs associated with responding to the attack.
- The attack could erode customer trust in CDK and its products, leading to a loss of market share.
- The cyberattack highlights the increasing vulnerability of the automotive industry to cyber threats, emphasizing the need for enhanced cybersecurity measures.
Prevention and Mitigation
CDK can take proactive measures to strengthen its cybersecurity posture and mitigate the risk of future attacks. By identifying potential vulnerabilities, implementing best practices, and leveraging industry advancements, CDK can enhance its overall security.
CDK should conduct thorough vulnerability assessments to identify weaknesses in its systems, networks, and applications. Regular patching and software updates can address known vulnerabilities and prevent attackers from exploiting them.
Security Awareness and Training
Employees are often the first line of defense against cyberattacks. CDK should invest in comprehensive security awareness and training programs to educate employees about cybersecurity threats, best practices, and reporting procedures. Regular phishing simulations and exercises can test employee preparedness and identify areas for improvement.
Multi-Factor Authentication
Implementing multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of identification when accessing sensitive systems or data. MFA can significantly reduce the risk of unauthorized access, even if attackers obtain user credentials.
Network Segmentation
Segmenting the network into smaller, isolated zones can limit the impact of a breach. By restricting access to specific resources and services, CDK can contain the spread of malware or unauthorized activity within its network.
Incident Response Plan
A well-defined incident response plan Artikels the steps to be taken in the event of a cyberattack. This plan should include clear roles and responsibilities, communication protocols, and procedures for containment, eradication, and recovery.
Industry Best Practices and Advancements
CDK should stay abreast of industry best practices and advancements in cybersecurity. Adopting emerging technologies, such as artificial intelligence (AI) and machine learning (ML), can enhance threat detection and response capabilities. Collaboration with cybersecurity experts and vendors can provide access to specialized knowledge and resources.
Amidst the ongoing investigation into the CDK cyberattack, news broke of the passing of former US President Jimmy Carter. Jimmy Carter passed away at the age of 98, leaving behind a legacy of peacemaking and humanitarian efforts. As the CDK cyberattack investigation continues, it is important to remember the resilience of our digital infrastructure and the need to protect it from future threats.
The recent cdk cyberattack update has sent shockwaves through the industry, highlighting the need for robust cybersecurity measures. In this context, the expertise of john force , a renowned cybersecurity expert, is invaluable. His insights on the latest threats and best practices can help organizations stay ahead of the curve and protect their valuable data from malicious actors.
As the cdk cyberattack update continues to unfold, it is imperative that we stay vigilant and adopt proactive measures to mitigate risks.
The recent update on the CDK cyberattack raises concerns about the security of critical infrastructure. While the investigation continues, it is essential to remember that cybersecurity remains a paramount issue. In the meantime, the passing of former President Jimmy Carter did jimmy carter pass serves as a reminder of the importance of leadership in times of crisis.
As the CDK cyberattack update unfolds, we must remain vigilant and work together to strengthen our defenses against future threats.